Safeguarding your cryptocurrency investments is paramount. This comprehensive guide on how to safely store your cryptocurrency will equip you with the knowledge to protect your digital assets from theft and loss. We’ll explore various cryptocurrency storage methods, including hardware wallets, software wallets, and exchanges, outlining their respective security features and risks. Learn best practices for private key management, password security, and two-factor authentication to ensure the safekeeping of your Bitcoin, Ethereum, and other valuable digital currencies. Discover how to mitigate threats and build a robust cryptocurrency security strategy.
Understanding Hot vs Cold Wallets
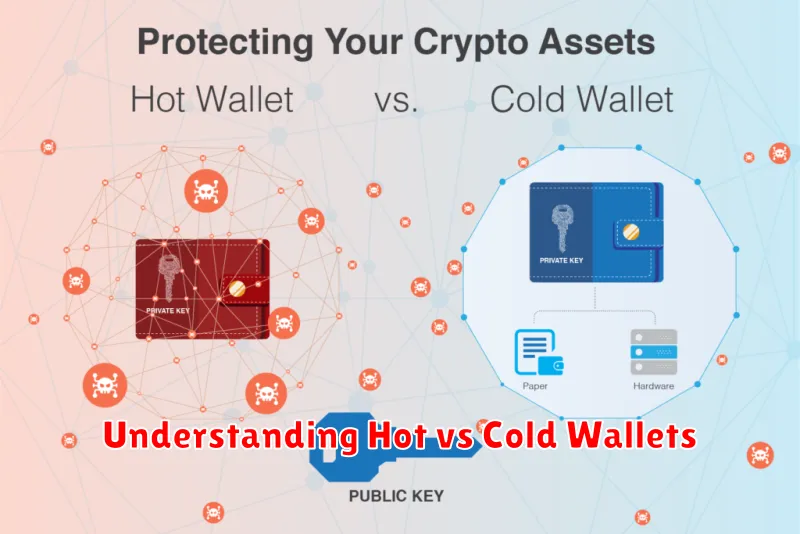
Choosing the right cryptocurrency wallet is crucial for security. The primary distinction lies in whether the wallet is connected to the internet (“hot”) or offline (“cold”).
Hot wallets, such as software wallets (desktop, mobile) and web wallets, offer convenience due to their constant online connectivity. This allows for quick and easy transactions. However, they are more vulnerable to hacking and malware, as they are constantly exposed to online threats. The risk increases with the amount of cryptocurrency stored.
Cold wallets, primarily hardware wallets, provide superior security. They are offline devices storing your private keys, significantly reducing the risk of cyberattacks. While offering enhanced security, they are less convenient for frequent transactions. Transactions require connecting the device to a computer and internet access, a process that may take longer.
The choice between hot and cold wallets depends on your individual needs and risk tolerance. For smaller amounts and frequent transactions, a hot wallet might suffice. For larger holdings or long-term storage, a cold wallet is generally recommended for its superior security.
Best Practices for Backup and Recovery

Regular backups are crucial for safeguarding your cryptocurrency. Implement a robust backup strategy, employing multiple methods for redundancy.
Consider using a combination of offline and online backups. Offline backups, such as hardware wallets or printed paper wallets, offer strong security against online threats. Online backups, while vulnerable to hacking, provide convenient access and redundancy.
Encryption is paramount. Always encrypt your backup files using strong, unique passwords to protect against unauthorized access.
Store backups in separate locations. Diversifying storage locations minimizes the risk of total data loss from a single point of failure, like a fire or theft. Consider using a safety deposit box or a geographically separate location.
Regularly test your recovery process. Ensure your backups are functional and accessible by periodically attempting a restoration. This allows for early detection and correction of any issues before a real crisis occurs.
Employ strong password management practices. Use a password manager to securely store your encryption keys and other crucial information, avoiding the risk of forgetting or losing access.
Keep your backup system updated. Regularly update your backup software and hardware to benefit from the latest security patches and improvements.
Document your backup strategy. Create clear, concise documentation detailing your backup process, storage locations, and recovery procedures for easy access if needed.
Securing Your Private Keys
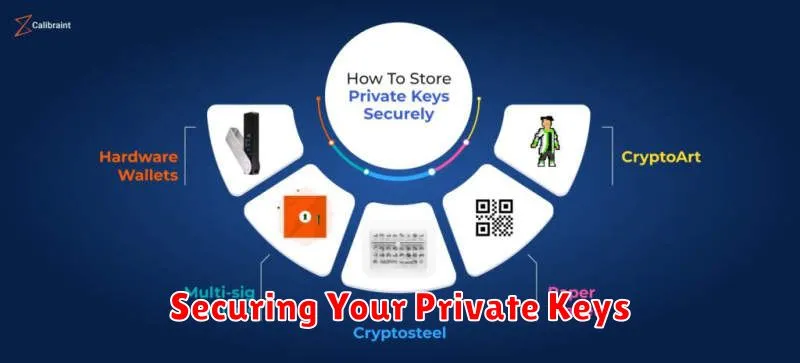
Private keys are the foundation of cryptocurrency security. Losing them means losing access to your funds, irrevocably. Therefore, securing them is paramount.
Avoid storing your private keys on devices connected to the internet. Hardware wallets offer the most secure offline storage. These dedicated devices isolate your keys from potential online threats.
If using a software wallet, choose reputable options and employ strong passwords. Regularly back up your wallet, storing the backups in multiple secure, offline locations. Never share your private keys with anyone.
Consider using a paper wallet. This involves printing your public and private keys offline. However, this method requires meticulous care to prevent physical damage or loss. Store paper wallets in a fireproof and waterproof safe.
Regularly review your security measures. Stay updated on best practices and security vulnerabilities to mitigate potential risks to your cryptocurrency holdings.
Avoiding Phishing Scams

Phishing scams are a major threat to cryptocurrency security. Phishing involves deceptive attempts to obtain sensitive information such as passwords, private keys, or seed phrases, usually by disguising as a trustworthy entity in electronic communication.
Never click on links or open attachments from unknown or suspicious senders. Always verify the sender’s identity independently before responding to any communication requesting personal information. Legitimate cryptocurrency exchanges and services will never request such information via email or unsolicited messages.
Be wary of emails or messages promising unrealistic returns or free cryptocurrency. These are common tactics used in phishing attempts. Double-check the URL of any website before entering your credentials. Phishing sites often mimic legitimate ones closely.
Enable two-factor authentication (2FA) on all your cryptocurrency accounts and exchanges. This adds an extra layer of security, making it much harder for phishers to access your accounts even if they obtain your password.
Regularly review your account statements and transaction history for any unauthorized activity. Report any suspicious activity immediately to the relevant exchange or service provider.
By remaining vigilant and employing these simple precautions, you can significantly reduce your risk of falling victim to phishing scams and better protect your cryptocurrency investments.
Using Multi-Signature Authentication
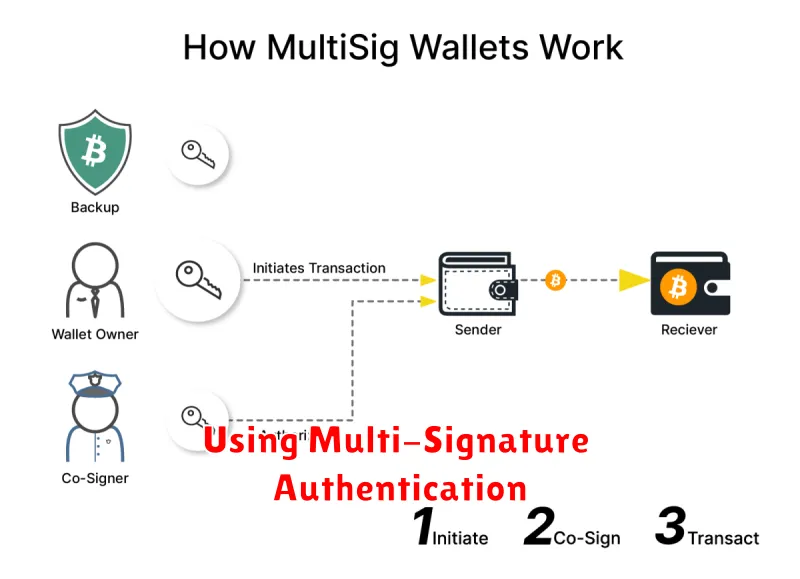
Multi-signature authentication enhances the security of your cryptocurrency by requiring multiple private keys to authorize a transaction. This significantly reduces the risk of unauthorized access and theft. Instead of a single point of failure, multiple parties (or devices) must collaborate to approve any transaction.
How it works: You distribute your private keys across different devices or individuals. A transaction only proceeds if a predetermined number of these keys (e.g., 2 out of 3) sign it. This setup makes it exponentially more difficult for hackers to steal your funds, even if they compromise one of your keys.
Benefits: Increased security against theft, loss, or compromise of a single private key. Improved control, as multiple individuals can authorize transactions, potentially preventing fraudulent activity. Enhanced trust, particularly useful for businesses or shared wallets.
Considerations: Implementing multi-signature authentication requires careful planning and coordination. Losing access to even one required key can render your funds inaccessible. Consider the implications of key loss and have a recovery plan in place. The added complexity may also introduce slight delays in transaction processing.

